Network Security
Modern Network Security Solution with Sophos
Objective
To provide a robust, scalable, and cost-effective network security solution that safeguards the organization's IT infrastructure against evolving cyber threats.
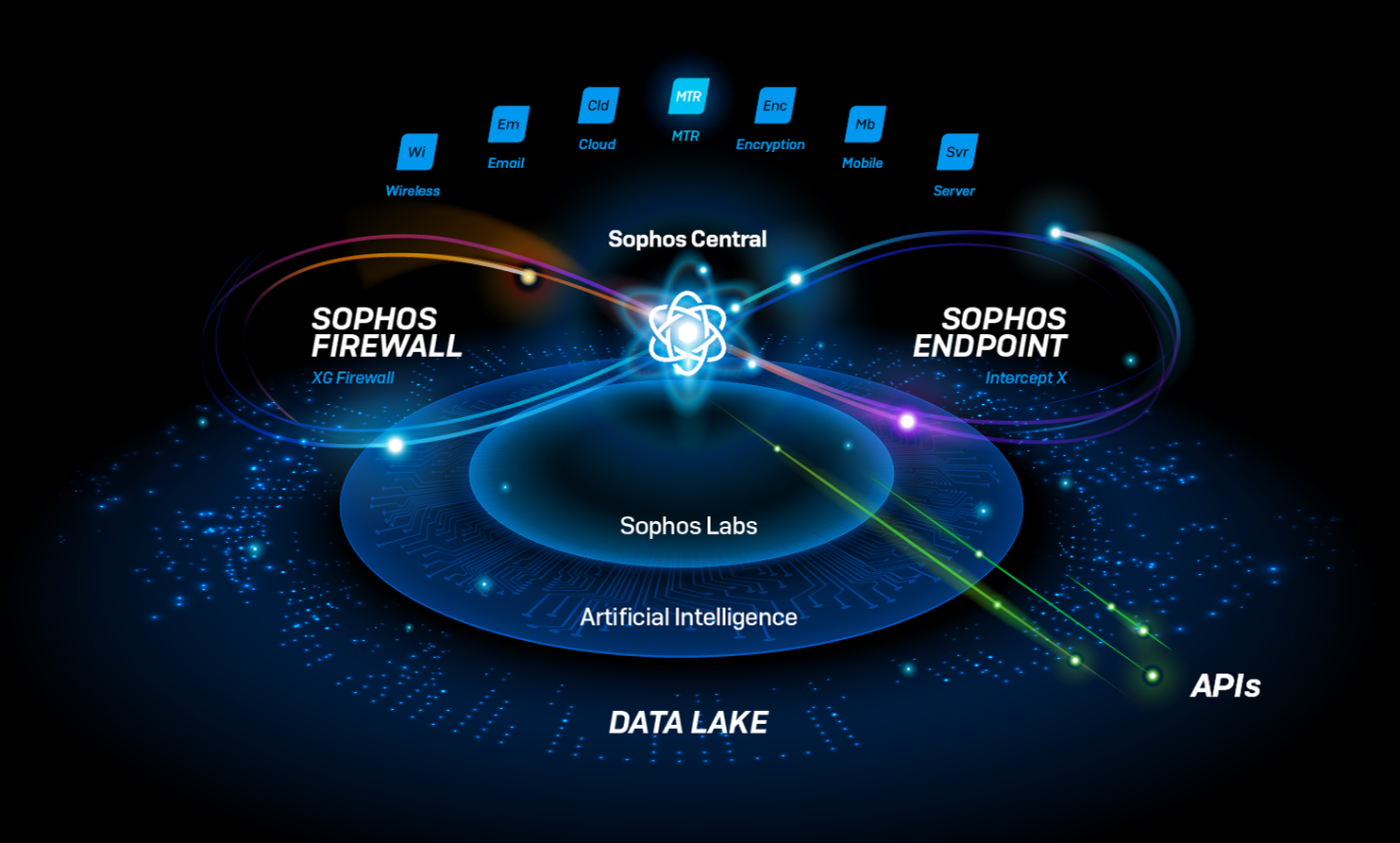
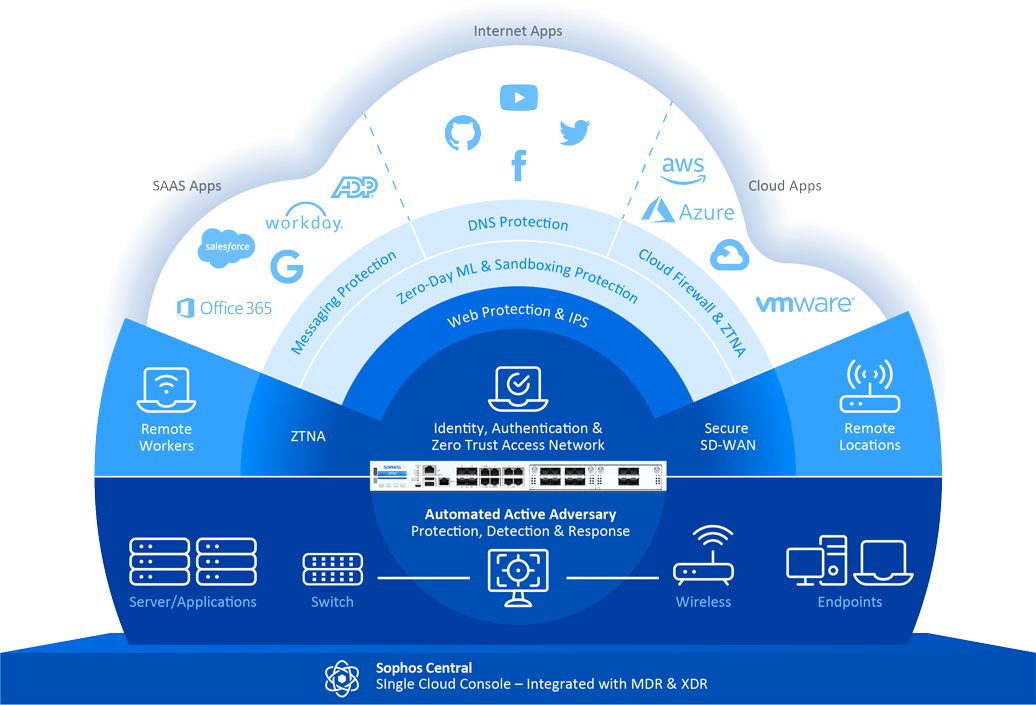
Core Components of the Solution
1. Perimeter Security with Sophos Firewall
- Key Features:
- Advanced threat protection (ATP) to block zero-day threats and ransomware.
- Deep packet inspection (DPI) engine for SSL/TLS encrypted traffic.
- Web application firewall (WAF) to secure internal applications.
- SD-WAN capabilities for optimized performance across distributed environments.
- User identity-based policies to enhance control and visibility.
- Deployment Options: Physical or virtual appliance, depending on organizational needs. High-availability mode for uninterrupted service.
2. Endpoint Protection with Sophos Intercept X
- Key Features:
- Anti-exploit technology to prevent common attack vectors.
- Behavioral-based ransomware detection.
- AI-powered threat detection using deep learning models.
- Root cause analysis for detailed incident insights.
- Seamless integration with Sophos XG Firewall for synchronized security.
- Deployment Options: Centralized management via Sophos Central for simplified deployment and policy control.
3. Wireless and Network Access Control
Sophos Access Points for secure wireless connectivity. Sophos NAC (Network Access Control) to enforce device compliance and limit unauthorized access.
4. Email Security with Sophos Email
- Protection against phishing, business email compromise (BEC), and spam.
- Time-of-click URL verification to detect malicious links.
- Advanced sandboxing to identify and isolate malicious attachments.
5. Cloud Security
- Integration with Sophos Cloud Optix for cloud workload protection.
- Visibility and compliance management across AWS, Azure, and Google Cloud platforms.
- Automated remediation of misconfigurations and vulnerabilities.
6. Security Operations (SOC) with Sophos Managed Threat Response (MTR)
- 24/7 threat hunting, detection, and response by a dedicated team.
- Proactive identification and neutralization of threats.
- Detailed reporting for transparency and compliance.
7. Training and Awareness
- Sophos Phish Threat to educate employees about phishing and other social engineering tactics.
- Simulated phishing attacks to improve user awareness and resilience.

Implementation Strategy
- Conduct a network security audit to identify vulnerabilities and gaps.
- Deploy Sophos XG Firewall at the perimeter and implement endpoint protection.
- Integrate email and cloud security solutions with existing infrastructure.
- Establish a centralized management console for streamlined administration.
- Train employees to recognize potential threats and respond appropriately.
Benefits
- Unified threat management through synchronized security solutions.
- Proactive defense against advanced threats and compliance with industry standards.





